Removing a Windows Azure Virtual Machine doesn't remove everything for you. This post is all about cleaning up with PowerShell after removing a Windows Azure VM
PowerShell (6)
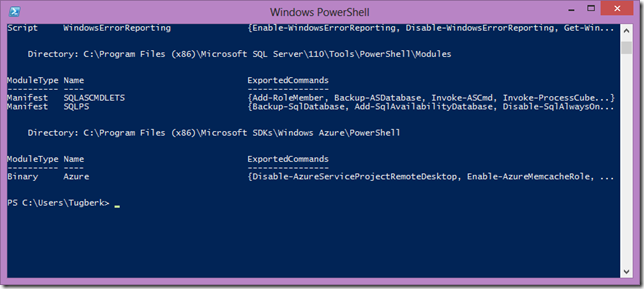
Windows Azure PowerShell Cmdlets is a great tool to manage your Windows Azure services but if you are like me, you would wanna know where all the stuff is going. This post is all about it.
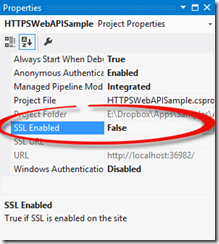
We will see how to smoothly work with IIS Express Self-signed Certificate, ASP.NET Web API and HttpClient by placing the self-signed certificate in the Trusted Root CA store.
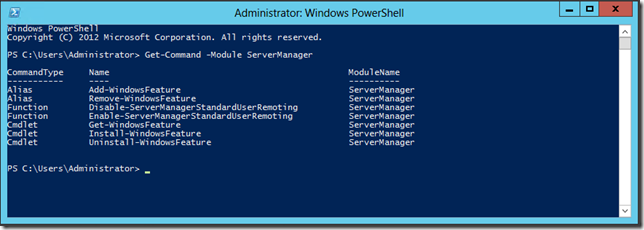
Script Out Everything - Initialize Your Windows Azure VM for Your Web Server with IIS, Web Deploy and Other Stuff
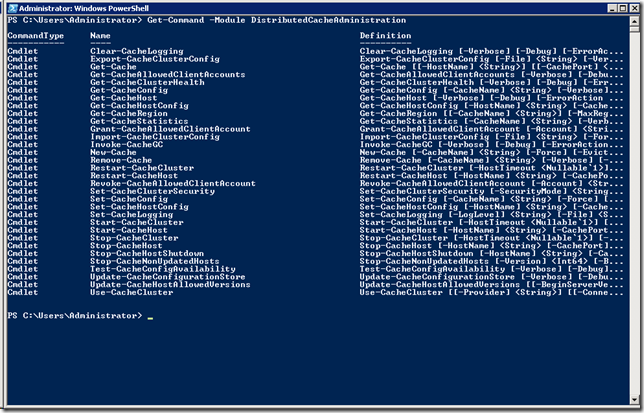
I started to use Windows Server AppFabric for its distributed caching feature and I wanted to take a note of the useful PowerShell commands to manage the service configuration and administration.
Deploying a Web Role with HTTPS Endpoint enabled with Self-Signed Certificate and a annoying problem of HTTPS input endpoint does not contain private key

