One of the missing pieces of the Windows Azure story is within our reach now! A few days ago Azure folks have released Windows Azure .NET Management Client Libraries
Windows Azure (10)
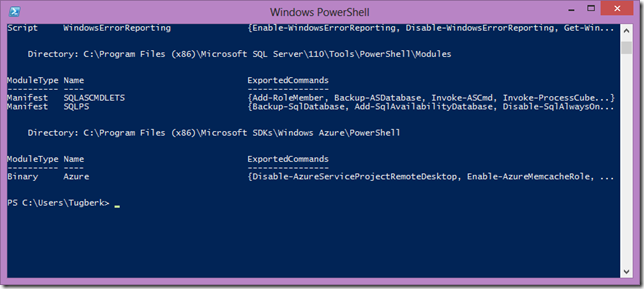
Removing a Windows Azure Virtual Machine doesn't remove everything for you. This post is all about cleaning up with PowerShell after removing a Windows Azure VM
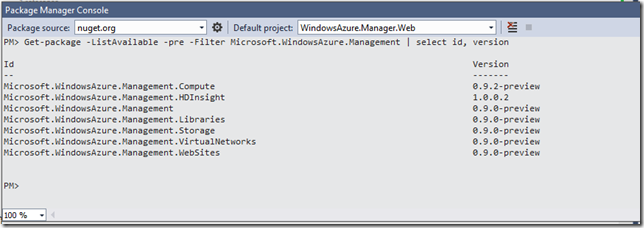
Windows Azure PowerShell Cmdlets is a great tool to manage your Windows Azure services but if you are like me, you would wanna know where all the stuff is going. This post is all about it.

Global Windows Azure Bootcamp will be happening on the 27th of April, 2013 all over the World and Microsoft Istanbul office will also be hosting one of these events.

One leg of Microsoft Web Camps spring 2013 tour will be held in Microsoft Istanbul office on the 6th of April, 2013.
I listed some resources on asynchronous programming for .NET server applications with C# which consist of blog posts, presentations and podcasts.
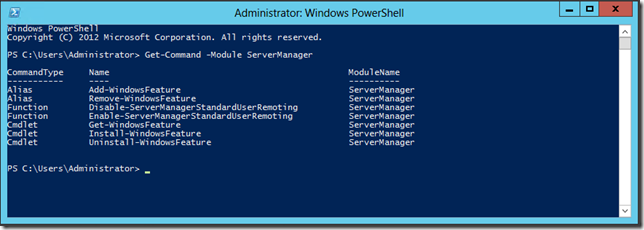
Script Out Everything - Initialize Your Windows Azure VM for Your Web Server with IIS, Web Deploy and Other Stuff
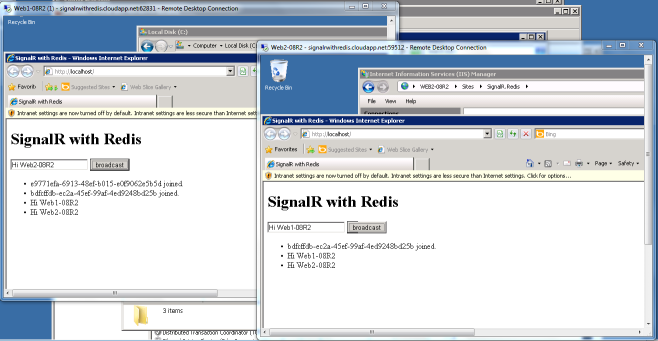
I just committed my first contribution to SignalR project: SignalR with Redis Running on a Windows Azure Virtual Machine. Enjoy :)
Deploying a Web Role with HTTPS Endpoint enabled with Self-Signed Certificate and a annoying problem of HTTPS input endpoint does not contain private key
This blog post provides a Windows Azure Blob Storage example which walks you through on how to use Blob Storage service with ASP.NET MVC.

